A new family of Android ransomware has been discovered that goes deeper into devices by using SMS messaging, according to security researchers. The ransomware, dubbed Android/Filecoder.C, has largely been distributed through various online forums, including XDA Developers and Reddit. Mostly, the attackers have been spotted luring potential victims into downloading adult content from suspicious links that set the pitch for the ransomware attack and demand a ransom ranging between $98 to $188 (roughly Rs. 6,800 to Rs. 13,000).
Security researchers at ESET have reported the arrival of the Android/Filecoder.C ransomware that is being transmitted through malicious apps. The malicious app links have been spotted by the researchers on some forum posts that were mostly related to porn content.
Once the infected apps are installed, the ransomware, which is believed to be active since at least July 12, attempts to spread via SMS messages that it sends to the victim’s contact list. The messages contain links to the ransomware to increase the interest of potential victims, and each of the links is advertised as an app that uses the photos of the recipient, the security researchers note in a blog post.
The ransomware is also said to have 42 different language versions of the single message template that it chooses depending on the language settings of the infected device. The researchers have also mentioned that once the link available in the sent message is clicked, the malicious app is installed. The app often displays a sex simulator, though it silently spreads malicious messages and implements the encryption or decryption in the background.
“The ransomware has the ability to send text messages, due to having access to the user’s contact list. Before it encrypts files, it sends a message to each of the victim’s contacts,” the researchers said in the post.
Once it completes the message sending process, the ransomware goes through the files available on the accessible storage and then encrypts most of them. The app that brings the ransomware includes hardcoded command-and-control (C2) settings and Bitcoin wallet addresses that are used to process ransom. Also, the attackers use Pastebin as a conduit to dynamically retrieve the information from the source code.
The ransomware is claimed to encrypt various file types, including general text files and images. However, it doesn’t grab typical Android extensions such as .apk and .dex as well as compressed files that are based on .zip and .rar formats.
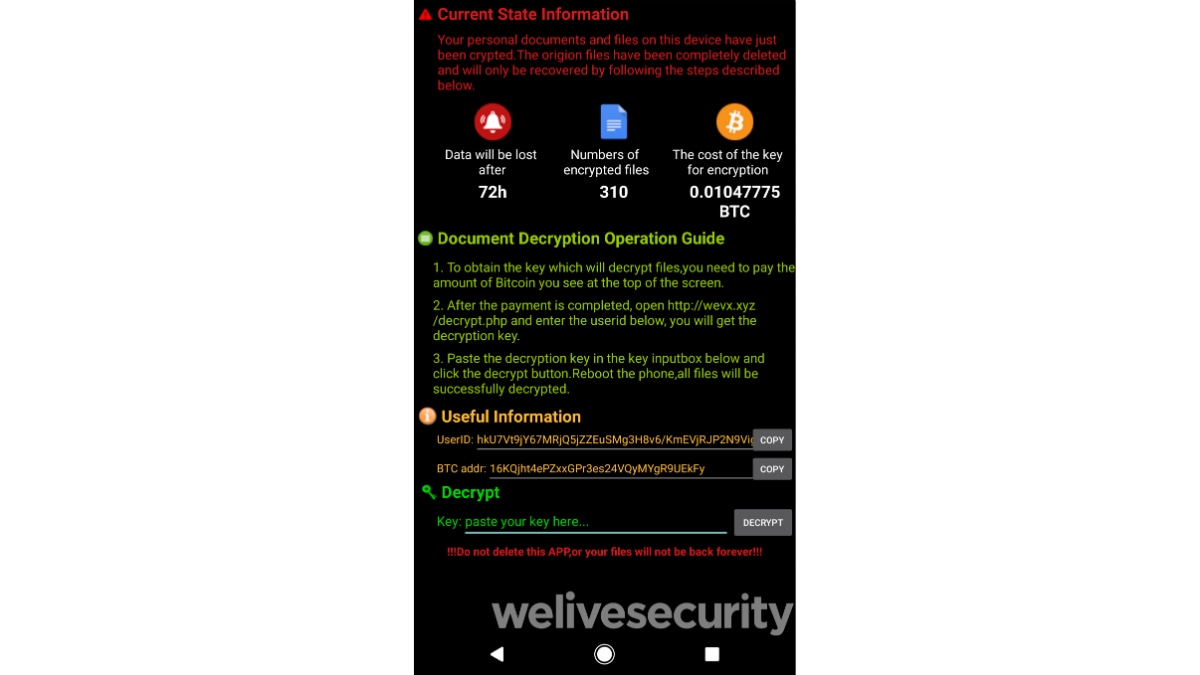
Android/Filecoder.C ransomware encrypts specific files to demand ransom
Photo Credit: WeLiveSecurity
According to the researchers, the encryption list of the latest Android ransomware looks identical to what was associated with Windows-focussed WannaCry.
Instead of completely blocking access to the device, Filecoder.C encrypts specific content and displays the ransom note. It also generates a public and private key pair where the private key is encrypted with an RSA algorithm and a hardcoded value. This enables the attacker to remotely decrypt the private key once it receives the demanded ransom amount from the victim.
Users are recommended to download apps from Google Play to avoid chances of being attacked. Also, it is advisable to avoid tapping unknown links and keep the devices up to date.
